Attackers continue to refine their tactics, targeting critical systems and holding sensitive data hostage. For firms that rely on uninterrupted access to trading platforms, payment systems and client records, even a short outage can cause significant disruption.
For financial services firms, where confidence and trust underpin client relationships, ransomware is one of the most pressing operational risks today. The threat has evolved from isolated attacks into a systemic business challenge that can disrupt operations, damage reputations, and attract regulatory scrutiny.
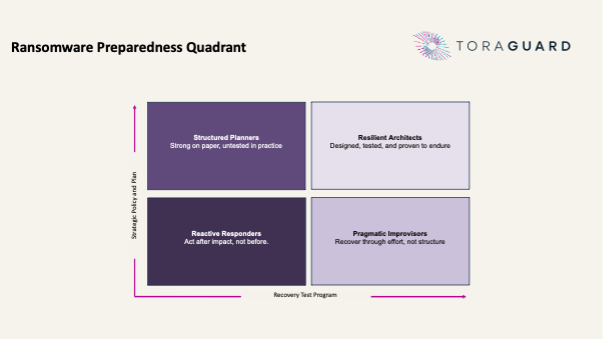
Yet the real test is not whether an attack occurs, but how well a firm is prepared to withstand and recover from it. Preparedness is the difference between a costly crisis and a contained incident. For senior executives, ransomware preparedness is no longer a purely technical issue. It is a strategic question that touches investor confidence, regulatory compliance and long-term resilience.